Traditional security methods are increasingly insufficient against evolving cyber threats. Leveraging open-source intelligence (OSINT) now plays a crucial role in tracking adversaries and can enhance your ability to preempt cyber threats.
In today's complex digital threat landscape, leveraging traditional security operations center techniques to mitigate advanced cyber threats is no longer enough. Adversaries' tactics and strategies are continually advancing and their resources are growing due to their successful cyberattacks, such as ransomware. These boosts in resources help them hire advanced programmers to create sophisticated malware and utilize advanced IT infrastructure to execute and conceal their cyberattacks.
In this article, I will discuss leveraging open-source intelligence (OSINT) techniques to hunt digital adversaries before they attack your organization. However, before we start, it's worth mentioning why adversary tracking and research are critical for cyber threat intelligence (CTI) professionals.
Why is adversary tracking important for the success of CTI professionals' work?
Adversary tracking and research facilitate CTI work through the following:
Understand the digital threat landscape
The digital threat landscape is continually evolving, and it does not stop at targeting high-profile organizations; it also targets individuals, government entities and non-profit organizations. For instance, the following threats are continually evolving. Lately, they have become boosted by the advancement of artificial intelligence (AI) technology, which aids cyberattackers in crafting more advanced attacks and automating repetitive tasks to execute more persuasive attacks.
- Malware
- Social engineering attacks (especially phishing)
- Hacking
- Distributed Denial of Service attacks (DDoS)
- Zero-day attacks
- AI-powered attacks which use machine learning (ML) to create more sophisticated phishing emails
- Supply chain attacks target vulnerabilities in the software supply chain to infiltrate multiple organizations at once
- Cloud security challenges that exploit misconfigurations and vulnerabilities in cloud environments to steal confidential data from target organizations
All these threats require a proactive approach to stop them instead of relying on traditional defense approaches and rule-based security solutions.
Proactive defense
Proactive defense has become a critical component in any cyber defense strategy. For instance, it helps CTI to anticipate cyberattacks before they happen and implement the necessary defense procedures and tools to mitigate them appropriately.
Attribute cyberattacks to their source
There are different threat actors—nation-state actors commonly back sophisticated attacks that require extensive resources. Organized criminal groups are also active and specialized in launching ransomware and phishing and providing cyberattacks on a subscription basis – such as malware-as-a-service and ransomware-as-a-service.
By knowing how to research adversaries, CTI professionals can better identify threat actors and prevent them executing attacks.
Help incident response teams
Incident response teams need every piece of information to understand who is behind ongoing cyberattacks. This knowledge helps them identify the scope of the attack and better understand how to investigate it. For example, knowing which cyberattacker group is behind a ransomware attack helps incident response teams understand their motivation, capabilities and what they are looking for so they can plan their recovery activities accordingly.
Predict future attacks
Cybercriminals leverage dark web networks like TOR and I2P to plan future attacks and communicate and collaborate anonymously. By monitoring threat actors' activities and discussions on the dark web and other criminal discussion forums, CTI professionals can better understand motivations and plans and organize their defense strategies to halt attacks before they start.
Adversary profiling
Tracking adversaries' activities is not enough to predict their future targets. Adversary profiling is a critical element within the CTI defense strategy because it allows CTI professionals to formulate a comprehensive picture of the adversary, including:
Capabilities - What tools, techniques and resources are at their disposal? For example, the type of IT infrastructure (servers, domain names, IP ranges) the adversary typically uses to execute their attacks
Motivations - What motivates adversaries to execute their attacks? (Ex. nation-state actors, ideological goals, hacktivists such as environmental activists or cybercriminals working for financial gain)
Preferred targets - What targets are the adversaries focusing on and prefer? (Ex. government agencies, non-profit organizations, banks, insurance companies, healthcare providers, etc.)
TTPs (Tactics, Techniques and Procedures) - What are their preferred tools and techniques to execute their attacks? When do they typically launch their attacks (date, time of the day, during holidays)? How have their attack tactics evolved?
Relationships - What relations do they have with other adversary groups?
Understanding these aspects about potential adversaries enables security teams to tailor their defenses addressing the specific threats posed by those particular adversaries.
Using OSINT for adversary tracking
OSINT has become a critical component in tracking adversaries in the CTI context. Here are the main areas of using OSINT for adversary tracking:
Social media intelligence (SOCMINT)
SOCMINT is the practice of collecting intelligence from social media platforms. Threat actors use social media platforms, especially closed Telegram groups and Reddit discussion forums, to discuss attack techniques and exchange information and expertise. By monitoring adversaries' activities on social media, CTI professionals can acquire actionable intelligence to help them predict adversaries' next move or future attack plans.
For example, CTI professionals can search for mentions of a particular threat actor group name across social media platforms and track their members' activities. Here are some services to monitor mentions across the web:
- Social Searcher - Social media search engine
- Google Alerts - Monitor the web for mentions or keywords set by the user
- Maltego - For mapping connections between social media accounts
- BoardReader - Allows searching across various blogs, open forums and message boards for specific mentions or names
- Searx - A meta-search engine that aggregates results from more than 70 search services
Domain and IP analysis
By analyzing domains and IPs associated with malicious attacks, OSINT gatherers can identify the following:
- Sources of attacks, such as country or region, can help in understanding the geopolitical context of threats.
- CTI professionals can use malicious IPs and domains stored in a comprehensive database to predict future attacks and prevent malicious connections from suspicious servers. This helps prevent phishing emails from entering an organization's internal network and blocking communication with command and control servers (C&C) used in ransomware attacks.
- Predict adversaries' capabilities by connecting different IPs and domains to reveal relationships between adversaries, potentially uncovering larger threat networks or IT infrastructure.
Here are some tools for domain and IP analysis:
- WHOIS - Retrieve WHOIS records
- DomainTools - WHOIS records
- ViewDNS.info - Retrieve various technical information about IPs and domain names, such as Reverse IP and domain lookup, reverse MX lookup, traceroute and IP history
- Whoxy - WHOIS history
- Robtex - Research IP numbers and domain names
- AbuseIPDB - A database containing IP addresses and domains that participated in hacking attempts or other malicious activities (see Figure 1)
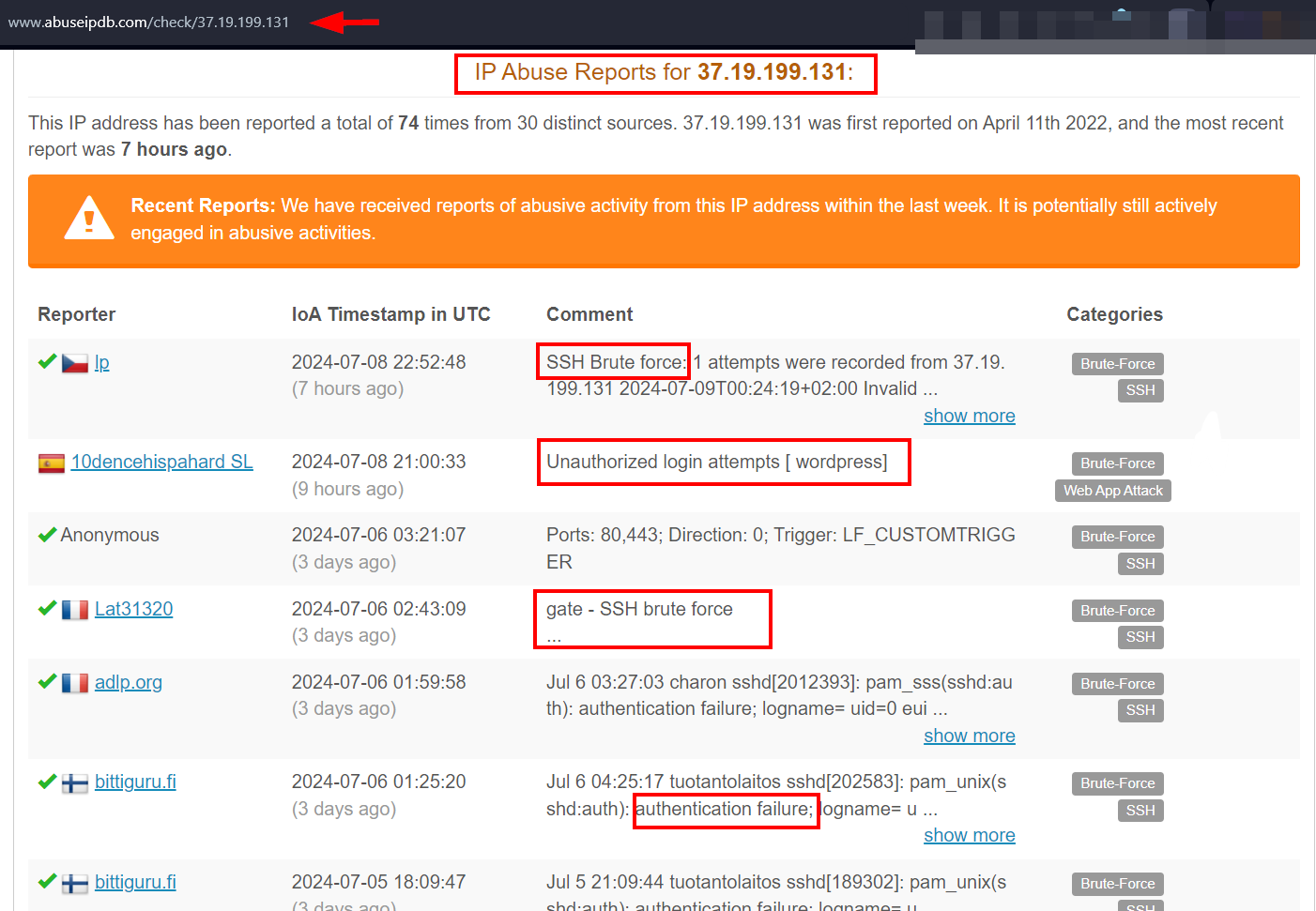
Figure 1 - Check if an IP address of a domain name is involved in malicious activities
- BLACKLIST CHECK from MXTOOLBOX - Test a mail server IP address against over 100 DNS-based email blacklists
Malware analysis
Malware analysis is a key component of CTI and proactive cybersecurity for the following reasons:
Understanding adversary capabilities
Examining malware samples gives CTI professionals insight into understanding adversary capabilities and resources. After dissecting them, they can comprehend how malware works and develop appropriate solutions to stop them.
Identification of new malware strains
This knowledge is necessary to develop mitigation techniques and prevent attacks from becoming widespread. It allows security teams to stay ahead of emerging threats.
Predicting future attacks
By understanding how new malware works and communicates with its operators, security teams can better understand their internal architecture and develop proactive solutions early to stop similar attacks.
Revealing attackers' IT infrastructure
By identifying IP addresses and domains associated with a particular malware attack, in addition to attackers' persistence techniques, security teams can track this information to reveal who is behind malware attacks.
Here are some tools to perform malware analysis:
- Cuckoo Sandbox - An open-source dynamic malware analysis program
- Joe Sandbox Basic - Conduct in-depth malware analysis and examine potentially malicious files and URLs across Windows, macOS and Linux platforms
- Ghidra - An open-source reverse engineering (SRE) suite of tools developed by NSA
- Wireshark - An open-source network protocol analyzer
- The Volatility Framework - Memory analysis tool
- Virustotal - An online service that analyzes suspicious files, domains, IPs and URLs to detect malware
Paste sites monitoring
Adversaries commonly leverage paste sites to share data dump samples and other leaked information. Paste websites provide early indicators of data breaches and can be used effectively to warn affected parties to take immediate measures to prevent further attacks against their IT systems.
Here are some popular paste websites to monitor:
- Pastebin - A popular paste website
- GitHub Gist - A free website for sharing code, notes and snippets
- PasteHunter - Scan and search many Pastebin websites
Dark web intelligence
Dark web intelligence plays a critical role in CTI by providing insights into the hidden world of cybercrime. Here's how monitoring dark web forums and illegal marketplaces helps in threat detection and mitigation:
Provide early warning signs against cybercrime
Dark web discussion forums are commonly used to discuss new exploits and software vulnerabilities before they become widely known. On the other hand, new hacking tools, exploits and potential targets are also discussed in such places. This information provides critical context and technical information about future attacks for CTI professionals.
Track stolen data
Dark web marketplaces are considered the virtual storefronts for cybercriminals, where they sell their stolen information, such as credit card details, login credentials or Personally Identifiable Information (PII) stolen from various breached websites. On the other hand, monitoring the seller profiles on the darknet marketplace may give some information about adversaries and help attribute cyberattacks to their real initiators, which helps understand their motivation and capabilities.
OSINT plays a vital role in modern CTI. By leveraging OSINT, CTI professionals can track adversaries, predict attack vectors and improve defensive strategies. The techniques discussed in this article—from social media monitoring to dark web intelligence—provide a comprehensive approach to threat actor profiling and tracking. However, it is important to remember that OSINT is just one piece of the CTI arsenal. Integrating OSINT methods with other intelligence sources is critical to effective threat analysis.
Remember to stay secure and anonymous while you research. Protect your identity and the intent of your investigation with a purpose-built digital investigations platform like Silo for Research.
Tags Dark web research OSINT research Threat intelligence
